- This cheat sheet lists a series of XSS attacks that can be used to bypass certain XSS defensive filters. Please note that input filtering is an incomplete defense for XSS which these tests can be used to illustrate. US-ASCII encoding (found by Kurt Huwig).This uses malformed ASCII encoding with 7.
- ASCII Character Codes Table & Cheat Sheet. Special Chars; 9 t (Tab): 10 (NL): 13 r (CR): 32: Space: 33! 34 ' 35 # 36 $ 37% 38 & 39 ' 40 (41) 42. 43 + 44, 45-46.
Pasted from an original notecard compiled by Gooden Uggla.
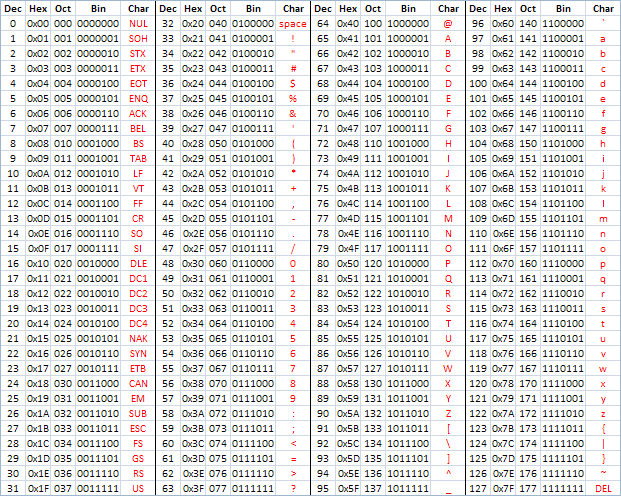
Cheat sheet for programmers with hex and binary, ascii chart, and calculator 0 = 0x0 = 0b0000 1 = 0x1 = 0b0001 2 = 0x2 = 0b0010 3 = 0x3 = 0b0011 4 = 0x4 = 0b0100 5 = 0x5 = 0b0101 6 = 0x6 = 0b0110 7 = 0x7 = 0b0111 8 = 0x8 = 0b1000 9 = 0x9 = 0b1001 10 = 0xA = 0b1010 11 = 0xB = 0b1011 12 = 0xC = 0b1100 13 = 0xD = 0b1101 14 = 0xE = 0b1110 15 = 0xF.
☺ ☻ ♥ ♦ ♣ ♠ • ◘ ○ ◙ ♂ ♀ ♪ ♫ ☼ ► ◄ ↕ ‼ ¶ ☀
☀ ☁ ☂ ☃ ☄ ★ ☆ ☇ ☎ ☏ ☙ ☚ ☛ ☜ ☝ ☞] U+261E ☞ WHITE RIGHT POINTING INDEX
[☟] U+261F ☟ WHITE DOWN POINTING INDEX
[☠] U+2620 ☠ SKULL AND CROSSBONES
[☡] U+2621 ☡ CAUTION SIGN
[☢] U+2622 ☢ RADIOACTIVE SIGN
[☣] U+2623 ☣ BIOHAZARD SIGN
[☤] U+2624 ☤ CADUCEUS
[☥] U+2625 ☥ ANKH
[☦] U+2626 ☦ ORTHODOX CROSS
[☧] U+2627 ☧ CHI RHO
[☨] U+2628 ☨ CROSS OF LORRAINE
[☩] U+2629 ☩ CROSS OF JERUSALEM
[☪] U+262A ☪ STAR AND CRESCENT
[☫] U+262B ☫ FARSI SYMBOL
Asciidoc Cheat Sheet
[☬] U+262C ☬ ADI SHAKTI
[☭] U+262D ☭ HAMMER AND SICKLE
[☮] U+262E ☮ PEACE SYMBOL
[☯] U+262F ☯ YIN YANG
[☸] U+2638 ☸ WHEEL OF DHARMA
[☹] U+2639 ☹ WHITE FROWNING FACE
[☺] U+263A ☺ WHITE SMILING FACE
[☻] U+263B ☻ BLACK SMILING FACE
[☼] U+263C ☼ WHITE SUN WITH RAYS
[☽] U+263D ☽ FIRST QUARTER MOON
[☾] U+263E ☾ LAST QUARTER MOON
[☿] U+263F ☿ MERCURY
[♀] U+2640 ♀ FEMALE SIGN
[♁] U+2641 ♁ EARTH
[♂] U+2642 ♂ MALE SIGN
[♃] U+2643 ♃ JUPITER
[♄] U+2644 ♄ SATURN
[♅] U+2645 ♅ URANUS
[♆] U+2646 ♆ NEPTUNE
[♇] U+2647 ♇ PLUTO
[♈] U+2648 ♈ ARIES
[♉] U+2649 ♉ TAURUS
[♊] U+264A ♊ GEMINI
[♋] U+264B ♋ CANCER
[♌] U+264C ♌ LEO
[♍] U+264D ♍ VIRGO
[♎] U+264E ♎ LIBRA
[♏] U+264F ♏ SCORPIUS
[♐] U+2650 ♐ SAGITTARIUS
[♑] U+2651 ♑ CAPRICORN
[♒] U+2652 ♒ AQUARIUS
[♓] U+2653 ♓ PISCES
[♔] U+2654 ♔ WHITE CHESS KING
[♕] U+2655 ♕ WHITE CHESS QUEEN
[♖] U+2656 ♖ WHITE CHESS ROOK
[♗] U+2657 ♗ WHITE CHESS BISHOP
[♘] U+2658 ♘ WHITE CHESS KNIGHT
[♙] U+2659 ♙ WHITE CHESS PAWN
[♚] U+265A ♚ BLACK CHESS KING
[♛] U+265B ♛ BLACK CHESS QUEEN
[♜] U+265C ♜ BLACK CHESS ROOK
[♝] U+265D ♝ BLACK CHESS BISHOP
[♞] U+265E ♞ BLACK CHESS KNIGHT
[♟] U+265F ♟ BLACK CHESS PAWN
[♠] U+2660 ♠ BLACK SPADE SUIT
[♡] U+2661 ♡ WHITE HEART SUIT
[♢] U+2662 ♢ WHITE DIAMOND SUIT
[♣] U+2663 ♣ BLACK CLUB SUIT
[♤] U+2664 ♤ WHITE SPADE SUIT
[♥] U+2665 ♥ BLACK HEART SUIT
[♦] U+2666 ♦ BLACK DIAMOND SUIT
[♧] U+2667 ♧ WHITE CLUB SUIT
[♨] U+2668 ♨ HOT SPRINGS
[♩] U+2669 ♩ QUARTER NOTE
[♪] U+266A ♪ EIGHTH NOTE
[♫] U+266B ♫ BEAMED EIGHTH NOTES
[♬] U+266C ♬ BEAMED SIXTEENTH NOTES
[♭] U+266D ♭ MUSIC FLAT SIGN
[♮] U+266E ♮ MUSIC NATURAL SIGN
[♯] U+266F ♯ MUSIC SHARP SIGN
[♰] U+2670 ♰ WEST SYRIAC CROSS
[♱] U+2671 ♱ EAST SYRIAC CROSS
[♲] U+2672 ♲ UNIVERSAL RECYCLING SYMBOL
[♻] U+267B ♻ BLACK UNIVERSAL RECYCLING SYMBOL
[♼] U+267C ♼ RECYCLED PAPER SYMBOL
[♽] U+267D ♽ PARTIALLY-RECYCLED PAPER SYMBOL
[⚀] U+2680 ⚀ DIE FACE-1
[⚁] U+2681 ⚁ DIE FACE-2
[⚂] U+2682 ⚂ DIE FACE-3
[⚃] U+2683 ⚃ DIE FACE-4
[⚄] U+2684 ⚄ DIE FACE-5
[⚅] U+2685 ⚅ DIE FACE-6
[⚆] U+2686 ⚆ WHITE CIRCLE WITH DOT RIGHT
[⚇] U+2687 ⚇ WHITE CIRCLE WITH TWO DOTS
[⚈] U+2688 ⚈ BLACK CIRCLE WITH WHITE DOT RIGHT
[⚉] U+2689 ⚉ BLACK CIRCLE WITH TWO WHITE DOTS
[✁] U+2701 ✁ UPPER BLADE SCISSORS
[✂] U+2702 ✂ BLACK SCISSORS
[✃] U+2703 ✃ LOWER BLADE SCISSORS
[✄] U+2704 ✄ WHITE SCISSORS
[✆] U+2706 ✆ TELEPHONE LOCATION SIGN
[✇] U+2707 ✇ TAPE DRIVE
[✈] U+2708 ✈ AIRPLANE
[✉] U+2709 ✉ ENVELOPE
[✌] U+270C ✌ VICTORY HAND
[✍] U+270D ✍ WRITING HAND
[✎] U+270E ✎ LOWER RIGHT PENCIL
[✏] U+270F ✏ PENCIL Curl post example.
[✐] U+2710 ✐ UPPER RIGHT PENCIL
[✑] U+2711 ✑ WHITE NIB
[✒] U+2712 ✒ BLACK NIB
[✓] U+2713 ✓ CHECK MARK
[✔] U+2714 ✔ HEAVY CHECK MARK
[✕] U+2715 ✕ MULTIPLICATION X
[✖] U+2716 ✖ HEAVY MULTIPLICATION X
[✗] U+2717 ✗ BALLOT X
[✘] U+2718 ✘ HEAVY BALLOT X
[✙] U+2719 ✙ OUTLINED GREEK CROSS
[✚] U+271A ✚ HEAVY GREEK CROSS
[✛] U+271B ✛ OPEN CENTRE CROSS
[✜] U+271C ✜ HEAVY OPEN CENTRE CROSS
[✝] U+271D ✝ LATIN CROSS
[✞] U+271E ✞ SHADOWED WHITE LATIN CROSS
[✟] U+271F ✟ OUTLINED LATIN CROSS
[✠] U+2720 ✠ MALTESE CROSS
[✡] U+2721 ✡ STAR OF DAVID
[✢] U+2722 ✢ FOUR TEARDROP-SPOKED ASTERISK
[✣] U+2723 ✣ FOUR BALLOON-SPOKED ASTERISK
[✤] U+2724 ✤ HEAVY FOUR BALLOON-SPOKED ASTERISK
[✥] U+2725 ✥ FOUR CLUB-SPOKED ASTERISK
[✦] U+2726 ✦ BLACK FOUR POINTED STAR
[✧] U+2727 ✧ WHITE FOUR POINTED STAR
[✩] U+2729 ✩ STRESS OUTLINED WHITE STAR
[✪] U+272A ✪ CIRCLED WHITE STAR
[✫] U+272B ✫ OPEN CENTRE BLACK STAR
[✬] U+272C ✬ BLACK CENTRE WHITE STAR
[✭] U+272D ✭ OUTLINED BLACK STAR
[✮] U+272E ✮ HEAVY OUTLINED BLACK STAR
[✯] U+272F ✯ PINWHEEL STAR
[✰] U+2730 ✰ SHADOWED WHITE STAR
[✱] U+2731 ✱ HEAVY ASTERISK
[✲] U+2732 ✲ OPEN CENTRE ASTERISK

[✳] U+2733 ✳ EIGHT SPOKED ASTERISK
[✴] U+2734 ✴ EIGHT POINTED BLACK STAR
[✵] U+2735 ✵ EIGHT POINTED PINWHEEL STAR
[✶] U+2736 ✶ SIX POINTED BLACK STAR
[✷] U+2737 ✷ EIGHT POINTED RECTILINEAR BLACK STAR
[✸] U+2738 ✸ HEAVY EIGHT POINTED RECTILINEAR BLACK STAR
[✹] U+2739 ✹ TWELVE POINTED BLACK STAR
[✺] U+273A ✺ SIXTEEN POINTED ASTERISK
[✻] U+273B ✻ TEARDROP-SPOKED ASTERISK

[✼] U+273C ✼ OPEN CENTRE TEARDROP-SPOKED ASTERISK
[✽] U+273D ✽ HEAVY TEARDROP-SPOKED ASTERISK
[✾] U+273E ✾ SIX PETALLED BLACK AND WHITE FLORETTE
[✿] U+273F ✿ BLACK FLORETTE
[❀] U+2740 ❀ WHITE FLORETTE
[❁] U+2741 ❁ EIGHT PETALLED OUTLINED BLACK FLORETTE
[❂] U+2742 ❂ CIRCLED OPEN CENTRE EIGHT POINTED STAR
[❃] U+2743 ❃ HEAVY TEARDROP-SPOKED PINWHEEL ASTERISK
[❄] U+2744 ❄ SNOWFLAKE
[❅] U+2745 ❅ TIGHT TRIFOLIATE SNOWFLAKE
[❆] U+2746 ❆ HEAVY CHEVRON SNOWFLAKE
[❇] U+2747 ❇ SPARKLE
[❈] U+2748 ❈ HEAVY SPARKLE
[❉] U+2749 ❉ BALLOON-SPOKED ASTERISK
[❊] U+274A ❊ EIGHT TEARDROP-SPOKED PROPELLER ASTERISK Mac os x 10.11 vmware.
[❋] U+274B ❋ HEAVY EIGHT TEARDROP-SPOKED PROPELLER ASTERISK
[❍] U+274D ❍ SHADOWED WHITE CIRCLE
[❏] U+274F ❏ LOWER RIGHT DROP-SHADOWED WHITE SQUARE
[❐] U+2750 ❐ UPPER RIGHT DROP-SHADOWED WHITE SQUARE
[❑] U+2751 ❑ LOWER RIGHT SHADOWED WHITE SQUARE
[❒] U+2752 ❒ UPPER RIGHT SHADOWED WHITE SQUARE
[❖] U+2756 ❖ BLACK DIAMOND MINUS WHITE X
[❘] U+2758 ❘ LIGHT VERTICAL BAR
[❙] U+2759 ❙ MEDIUM VERTICAL BAR
[❚] U+275A ❚ HEAVY VERTICAL BAR
[❛] U+275B ❛ HEAVY SINGLE TURNED COMMA QUOTATION MARK ORNAMENT
[❜] U+275C ❜ HEAVY SINGLE COMMA QUOTATION MARK ORNAMENT
[❝] U+275D ❝ HEAVY DOUBLE TURNED COMMA QUOTATION MARK ORNAMENT
[❞] U+275E ❞ HEAVY DOUBLE COMMA QUOTATION MARK ORNAMENT
[❡] U+2761 ❡ CURVED STEM PARAGRAPH SIGN ORNAMENT
[❢] U+2762 ❢ HEAVY EXCLAMATION MARK ORNAMENT
[❣] U+2763 ❣ HEAVY HEART EXCLAMATION MARK ORNAMENT
[❤] U+2764 ❤ HEAVY BLACK HEART
[❥] U+2765 ❥ ROTATED HEAVY BLACK HEART BULLET
[❦] U+2766 ❦ FLORAL HEART
[❧] U+2767 ❧ ROTATED FLORAL HEART BULLET
[❨] U+2768 ❨ MEDIUM LEFT PARENTHESIS ORNAMENT
[❩] U+2769 ❩ MEDIUM RIGHT PARENTHESIS ORNAMENT
[❪] U+276A ❪ MEDIUM FLATTENED LEFT PARENTHESIS ORNAMENT
[❫] U+276B ❫ MEDIUM FLATTENED RIGHT PARENTHESIS ORNAMENT
[❬] U+276C ❬ MEDIUM LEFT-POINTING ANGLE BRACKET ORNAMENT
[❭] U+276D ❭ MEDIUM RIGHT-POINTING ANGLE BRACKET ORNAMENT
[❮] U+276E ❮ HEAVY LEFT-POINTING ANGLE QUOTATION MARK ORNAMENT
[❯] U+276F ❯ HEAVY RIGHT-POINTING ANGLE QUOTATION MARK ORNAMENT
[❰] U+2770 ❰ HEAVY LEFT-POINTING ANGLE BRACKET ORNAMENT
[❱] U+2771 ❱ HEAVY RIGHT-POINTING ANGLE BRACKET ORNAMENT
[❲] U+2772 ❲ LIGHT LEFT TORTOISE SHELL BRACKET ORNAMENT
[❳] U+2773 ❳ LIGHT RIGHT TORTOISE SHELL BRACKET ORNAMENT
[❴] U+2774 ❴ MEDIUM LEFT CURLY BRACKET ORNAMENT
[❵] U+2775 ❵ MEDIUM RIGHT CURLY BRACKET ORNAMENT
[❶] U+2776 ❶ DINGBAT NEGATIVE CIRCLED DIGIT ONE
Asciidoctor Cheat Sheet
[❷] U+2777 ❷ DINGBAT NEGATIVE CIRCLED DIGIT TWO
[❸] U+2778 ❸ DINGBAT NEGATIVE CIRCLED DIGIT THREE
[❹] U+2779 ❹ DINGBAT NEGATIVE CIRCLED DIGIT FOUR
[❺] U+277A ❺ DINGBAT NEGATIVE CIRCLED DIGIT FIVE
[❻] U+277B ❻ DINGBAT NEGATIVE CIRCLED DIGIT SIX
[❼] U+277C ❼ DINGBAT NEGATIVE CIRCLED DIGIT SEVEN
[❽] U+277D ❽ DINGBAT NEGATIVE CIRCLED DIGIT EIGHT
[❾] U+277E ❾ DINGBAT NEGATIVE CIRCLED DIGIT NINE
[❿] U+277F ❿ DINGBAT NEGATIVE CIRCLED NUMBER TEN
[➀] U+2780 ➀ DINGBAT CIRCLED SANS-SERIF DIGIT ONE
[➁] U+2781 ➁ DINGBAT CIRCLED SANS-SERIF DIGIT TWO
[➂] U+2782 ➂ DINGBAT CIRCLED SANS-SERIF DIGIT THREE
[➃] U+2783 ➃ DINGBAT CIRCLED SANS-SERIF DIGIT FOUR
[➄] U+2784 ➄ DINGBAT CIRCLED SANS-SERIF DIGIT FIVE
[➅] U+2785 ➅ DINGBAT CIRCLED SANS-SERIF DIGIT SIX
[➆] U+2786 ➆ DINGBAT CIRCLED SANS-SERIF DIGIT SEVEN
[➇] U+2787 ➇ DINGBAT CIRCLED SANS-SERIF DIGIT EIGHT
[➈] U+2788 ➈ DINGBAT CIRCLED SANS-SERIF DIGIT NINE
[➉] U+2789 ➉ DINGBAT CIRCLED SANS-SERIF NUMBER TEN
[➊] U+278A ➊ DINGBAT NEGATIVE CIRCLED SANS-SERIF DIGIT ONE
[➋] U+278B ➋ DINGBAT NEGATIVE CIRCLED SANS-SERIF DIGIT TWO
[➌] U+278C ➌ DINGBAT NEGATIVE CIRCLED SANS-SERIF DIGIT THREE
[➍] U+278D ➍ DINGBAT NEGATIVE CIRCLED SANS-SERIF DIGIT FOUR
[➎] U+278E ➎ DINGBAT NEGATIVE CIRCLED SANS-SERIF DIGIT FIVE
[➏] U+278F ➏ DINGBAT NEGATIVE CIRCLED SANS-SERIF DIGIT SIX
[➐] U+2790 ➐ DINGBAT NEGATIVE CIRCLED SANS-SERIF DIGIT SEVEN
[➑] U+2791 ➑ DINGBAT NEGATIVE CIRCLED SANS-SERIF DIGIT EIGHT
[➒] U+2792 ➒ DINGBAT NEGATIVE CIRCLED SANS-SERIF DIGIT NINE
[➓] U+2793 ➓ DINGBAT NEGATIVE CIRCLED SANS-SERIF NUMBER TEN
[➔] U+2794 ➔ HEAVY WIDE-HEADED RIGHTWARDS ARROW
[➘] U+2798 ➘ HEAVY SOUTH EAST ARROW
[➙] U+2799 ➙ HEAVY RIGHTWARDS ARROW
[➚] U+279A ➚ HEAVY NORTH EAST ARROW
[➛] U+279B ➛ DRAFTING POINT RIGHTWARDS ARROW
[➜] U+279C ➜ HEAVY ROUND-TIPPED RIGHTWARDS ARROW
Hex To Ascii Cheat Sheet
[➝] U+279D ➝ TRIANGLE-HEADED RIGHTWARDS ARROW
[➞] U+279E ➞ HEAVY TRIANGLE-HEADED RIGHTWARDS ARROW
[➟] U+279F ➟ DASHED TRIANGLE-HEADED RIGHTWARDS ARROW
[➠] U+27A0 ➠ HEAVY DASHED TRIANGLE-HEADED RIGHTWARDS ARROW
[➡] U+27A1 ➡ BLACK RIGHTWARDS ARROW
[➢] U+27A2 ➢ THREE-D TOP-LIGHTED RIGHTWARDS ARROWHEAD
[➣] U+27A3 ➣ THREE-D BOTTOM-LIGHTED RIGHTWARDS ARROWHEAD
[➤] U+27A4 ➤ BLACK RIGHTWARDS ARROWHEAD
Ascii 176
[➥] U+27A5 ➥ HEAVY BLACK CURVED DOWNWARDS AND RIGHTWARDS ARROW
[➦] U+27A6 ➦ HEAVY BLACK CURVED UPWARDS AND RIGHTWARDS ARROW
[➧] U+27A7 ➧ SQUAT BLACK RIGHTWARDS ARROW
[➨] U+27A8 ➨ HEAVY CONCAVE-POINTED BLACK RIGHTWARDS ARROW
[➩] U+27A9 ➩ RIGHT-SHADED WHITE RIGHTWARDS ARROW
[➪] U+27AA ➪ LEFT-SHADED WHITE RIGHTWARDS ARROW
[➫] U+27AB ➫ BACK-TILTED SHADOWED WHITE RIGHTWARDS ARROW
[➬] U+27AC ➬ FRONT-TILTED SHADOWED WHITE RIGHTWARDS ARROW
[➭] U+27AD ➭ HEAVY LOWER RIGHT-SHADOWED WHITE RIGHTWARDS ARROW
[➮] U+27AE ➮ HEAVY UPPER RIGHT-SHADOWED WHITE RIGHTWARDS ARROW
[➯] U+27AF ➯ NOTCHED LOWER RIGHT-SHADOWED WHITE RIGHTWARDS ARROW
[➰] U+27B0 ➰ (unknown)
[➱] U+27B1 ➱ NOTCHED UPPER RIGHT-SHADOWED WHITE RIGHTWARDS ARROW
[➲] U+27B2 ➲ CIRCLED HEAVY WHITE RIGHTWARDS ARROW
[➳] U+27B3 ➳ WHITE-FEATHERED RIGHTWARDS ARROW
[➴] U+27B4 ➴ BLACK-FEATHERED SOUTH EAST ARROW
[➵] U+27B5 ➵ BLACK-FEATHERED RIGHTWARDS ARROW
[➶] U+27B6 ➶ BLACK-FEATHERED NORTH EAST ARROW
[➷] U+27B7 ➷ HEAVY BLACK-FEATHERED SOUTH EAST ARROW
[➸] U+27B8 ➸ HEAVY BLACK-FEATHERED RIGHTWARDS ARROW
[➹] U+27B9 ➹ HEAVY BLACK-FEATHERED NORTH EAST ARROW
[➺] U+27BA ➺ TEARDROP-BARBED RIGHTWARDS ARROW
[➻] U+27BB ➻ HEAVY TEARDROP-SHANKED RIGHTWARDS ARROW
[➼] U+27BC ➼ WEDGE-TAILED RIGHTWARDS ARROW
[➽] U+27BD ➽ HEAVY WEDGE-TAILED RIGHTWARDS ARROW
[➾] U+27BE ➾ OPEN-OUTLINED RIGHTWARDS ARROW
[⦁] U+2981 ⦁ Z NOTATION SPOT
[⦾] U+29BE ⦾ CIRCLED WHITE BULLET
[⦿] U+29BF ⦿ CIRCLED BULLET
[⧈] U+29C8 ⧈ SQUARED SQUARE
[⬅] U+2B05 ⬅ LEFTWARDS BLACK ARROW
Ascii Art Cheat Sheet
[⬆] U+2B06 ⬆ UPWARDS BLACK ARROW
Ascii Code Cheat Sheet

[⬇] U+2B07 ⬇ DOWNWARDS BLACK ARROW
| Symmetric [Performance] | CipherType | Asymmetric (Public Key) [Key Exchange] |
|---|---|---|
| Vernam (One Time Pad) Used in WWII in the German Enigma | XOR | RSA (Rivest, Shamir & Aldeman) - Uses large prime numbers. Encrypt/decrypt digital signatures. |
| AES (Advanced Encryption Standard) [Rijndael] (128, 192, 256 bits) Used by WPA2. (Data at rest) | Block | DSA (Digital Signature Algorithm) - Modifies Diffie-Hellman for use in digital signatures. Combines with elliptic curves to create ECDSA. |
| DES (Data Encryption Standard) [Lucifer] (56 bits) Easily brute forced. | Block | Diffie-Hellman Key Exchange (DH) - A standard for exchanging keys. Primarily used to send private keys over public networks. ECDHE (Elliptic Curve DH) Used for perfect forward secrecy. |
| 3DES (2 keys - 112 bits & 3 keys - 168 bits) Not used today. | Block | ECC (Elliptic Curve Cryptography) - Needs large integers composed of two or more large prime factors. Great for low powered machines bc uses less CPU. Uses curves instead of prime numbers. |
| RC4 (Rivest Cipher 4) (40-2048 bits) Used by WEP and WPA.[deprecated] | Stream | PGP (Pretty Good Privacy) - Used for emails and is used by IDEA algorithm; GPG(GNU Privacy Guard): A free version of PGP with sames specs. |
| Blowfish (1-448 bits) Fast, not patented limited. | Block | |
| Twofish (256 bits) | Block | Hashing Algorithms - Integrity |
| E0. Used by BlueTooth | Stream | MD5 (Message-Digest Algorithm v5) - 128 bit digest. Collision was found so it is not used as much. |
| SHA (Secure Hash Algorithm) - 160 bit digest. Standard today. Wnet from SHA-1(160 bit) to SHA-2(512 bit). by NSA. | ||
| Block cipher modes | HMAC (Hash-Based Message Authentication Code) - Combines itself with a symmetric key. Used in network encryption protocols. | |
| CBC (Cipher Block Chaining) - Symmetric, uses IV. Slow | RIPEMD (RACE Integrity Primitives Evaluation Message Digest) - Based on MD4. Collisions were found. | |
| GCM (Galois Counter Mode) - Encryption with auth. Very efficient. Provides data authenticity/intregrity. Widely used. | ||
| ECB (Electronic Code Book) - Simplest mode, each block with same key. Not recommended. | SSL (Secure Sockets Layer) protocol - Has two parts. The SSL Handshake Protocol establishes the secure channel. And the SSL Application Data Protocol is used to exchange data over the channel. 6 Steps in the handshaking process. | |
| CTR (Counter Mode) - Converts block into stream, uses IV. Widely used. | ISAKMP (Internet Security Association and Key Management Protocol) - Used to negotiate and provide authenticated keying material for security associations in a protected manner | |
| X.509 - A standard defining the format of public key certificates. Used in many Internet protocols, (TLS/SSL) and offline applications, like electronic signatures. Contains a public key and an identity, and is either signed by a CA or self-signed. | ||
| Wireless [Crypto protocols] | Perfect Forward Secrecy (PFS) - Prevents point of failure where a stolen private key can decrypt all connections by generating a new key each session. Protects past sessions against future compromises of secret keys. | |
| WPA (Wi-Fi Protected Access) - Uses RC4 with TKIP. Replaced by WPA2. | S/MIME, or Secure/Multipurpose Internet Mail Extensions, is a technology that allows you to encrypt your emails. S/MIME is based on asymmetric cryptography to protect your emails from unwanted access. | |
| WPA2 (WPA v2) - Uses CCMP for encryption and AES. | ||
| CCMP (Counter Mode with Cipher Block Chaining Message Authentication Code Protocol) - Is based on 128-bit AES. | ||
| TKIP (Temporal Key Integrity Protocol) - Mixes a root key with an IV, a new key for each packet. Prevents replay attacks and protects against tampering. | ||
| WEP (Wired Equivalent Privacy) | ||
| Goals of Cryptography | ||
| Wireless [Auth protocols] | Confidentiality - Asymmetric (Public Key) & Symmetric Encryption | |
| EAP (Extensible Authentication Protocol): Authentication framework that provides general guidance for authentication methods. | Authenticity/Authentication/Accountability - Asymmetric Encryption (Private Key), MAC/MIC, & Digital Signature | |
| PEAP (Protected EAP): An extension of EAP that is sometimes used with 802.1x, a certificate is required on the 802.1x server. | Integrity - Hashing, Checksum, Parity and Check Digit | |
| EAP-FAST (EAP Flexible Authentication with Secure Tunneling): A Cisco-designed replacement for Lightweight EAP, supports certificates. | Non-Repudiation - Digital Signature (Only) | |
| EAP-TLS (EAP Transport Layer Security): One of the most secure EAP standards and is widely implemented on many networks. It uses PKI, so certificates are required on the 802.1x server and on the clients. | ||
| EAP-TTLS (EAP Tunneled TLS): Allows for systems to use older authentication methods such as PAP within a TLS tunnel. Certificate is required on the 802.1x server but not on the clients. | Diffusion - Changing one character causes the plaintext to drastically change the outputed cipher. | |
| IEEE 802.1x: An authentication protocol used in VPNs, wired and wireless networks. In VPNs it is used as a RADIUS server, wired use it as a port-based authentication, and wireless use it in Enterprise mode. Can be used with certificate-based authentication. | Obfuscation: Taking something and making it difficult to understand, however it is not impossible to convert it back to the original form. | |
| RADIUS Federation: Members of one organization can authenticate to the network of another network using their normal credentials. Uses 802.1X as authentication method. | Confusion - The cipher doesn’t look anything like the plain text. | |
| Public key infrastructure | ||
| Stapling: Combining related items in order to reduce communication steps. The device that holds the certificate will also be the one to provide status of any revocation. | CA (Certificate Authority): A trusted third-party agency that is responsible for issuing digital certificates. | |
| Pinning: The application has hard-coded the server’s certificate into the application itself. | Intermediate CA (Intermediate Certificate Authority): An entity that processes the CSR and verifies the authenticity of the user on behalf of a CA. | |
| CRL (Certificate Revocation List): A list of certificates that are no longer valid, expired, or that have been revoked by the issuer. | ||
| Cert formats | CSR (Certificate Signing Request): A user request for a digital certificate. | |
| DER (Distinguished Encoding Rules): Are common and designed for X.509 certificates, they are used to extend binary encoded certificates. Cannot be edited by a plain text editor. Used with Java commonly. Stores single certificates, certificate chains, or private keys. Uses either a .der or .cer extension. | OCSP (Online Certificate Status Protocol): A request and response protocol that obtains the serial number of the certificate that is being validated and reviews revocation lists for the client. | |
| PEM (Privacy Enhanced Mail): It may contain single certificates, certificate chains, or private keys. Comes in a number of different file extensions: .pem, .crt, .cer, and .key. | Certificate: Digitally signed statement that associates a public key to the corresponding private key. | |
| CER (Certificate File): May be encoded as binary DER or as ASCII PEM. | Object identifiers (OID): A serial number that authenticates a certificate. | |
| P12: Is a PFX extension used in windows. | ||
| PKCS #12 (Public Key Cryptography Standards #12): It may contain single certificates, certificate chains, or private keys, although in most cases it is used to store public/private key pairs. Fully encrypt all the data in the file and require a password to open them. Uses the extension .pfx or .p12. | ||
| RFC (Remote Function Call): A formal document describes the specifications for a particular technology, was drafted by the Internet Engineering Task Force. | ||
| P7B: Is stored in Base64 ASCII, containing certificates and chains but not the private key. |
| Port | Use |
|---|---|
| 21 | FTP |
| 22 | SSH/SCP |
| 23 | Telnet |
| 25 | SMTP |
| 53 | DNS |
| 67-68 | DHCP |
| 80 | HTTP |
| 110 | POP3 |
| 143 | IMAP4 |
| 161 | SNMP |
| 389(default)-636(secured) | LDAP |
| 443 | HTTPS/SSL |
| UDP 1701 | L2TP |
| TCP 1723 | PPTP |
| 3389 | RDP |
| 137 | NetBIOS |
| UDP 123 | NTP |
Ascii Cheat Sheet
| BIA (Business Impact Analysis) | RTO (Recovery Time Objective) - The start of the interruption and time to establish recovery and end when you can successfully release the service back to your users. |
| MTTR (Mean Time to Recover) - The average time it takes to control and remediate a threat. | RPO (Recovery Point Objective) - Last available restore backup and the maximum time between backups being safely stored offsite. |
| MTBF (Mean Time Before Recover) - The average time between failures. | SLA (Service level agreement) - Defines the level of service expected by a customer from a supplier, laying out the metrics by which that service is measured, and the remedies or penalties, if any. |
| MTTF (Mean Time to Failure) - The length of time you can expect a device to remain in operation before it fails. |
